Computing
-
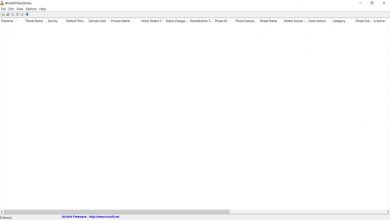
Check Windows threats with WinDefThreatsView, it’s free
Security is a fundamental factor for users. There are many risks that we can face when we access the network.…
Read More » -

Pentesting: how to start in this world
Computer security penetration tests, better known as Penetration Testing or Pentesting, are no longer impossible to learn and understand. Gone…
Read More » -

MAC Flooding: what is this technique that compromises our network
Computer attacks on the network can be very different and have different objectives. Some are designed to steal information and…
Read More » -

What are the most used ports to hack servers
As we know, servers are essential for Internet connections. They are essential for games, communications, email, web pages in general.…
Read More » -
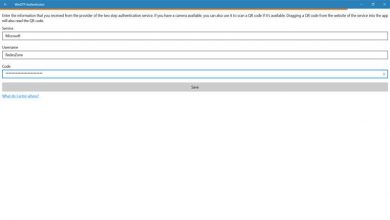
WinOTP Authenticator – Open Source Alternative to Set Up Two-Step Verification
Protecting our accounts and avoiding intruders is essential. We already know that security and privacy are fundamental aspects in these…
Read More » -
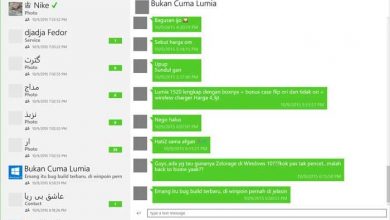
Boost your experience with telegram with these alternative clients
Telegram has become little by little and in the shadows the great alternative to WhatsApp as an instant messaging application.…
Read More » -
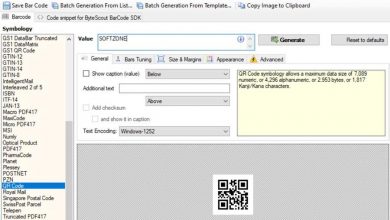
Create and design qr codes in windows with these programs and websites
Although at first it may seem a bit strange to some, the truth is that at this point the use…
Read More » -
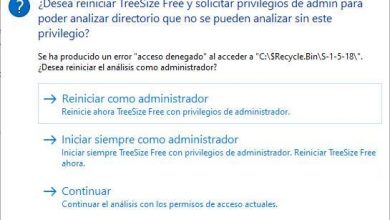
Running programs without administrator rights with runwithrestrictedrights
Surely on more than one occasion we have encountered the problem that we have downloaded a new application in Windows…
Read More » -

Turn your pc into a retro-console with these operating systems
Although today we can find thousands of games for PC and consoles, of all kinds, the most veteran players continue…
Read More » -

Revive guitar hero and rock band on your pc thanks to clone hero
If you like music games you have surely played, or at least know, the two most popular: Rock Band and…
Read More »
