Pentesting: how to start in this world

Computer security penetration tests, better known as Penetration Testing or Pentesting, are no longer impossible to learn and understand. Gone are the years when this type of knowledge was reserved only for experts who had to design their own tools. Today, using the right tools (and knowing what you have to do), we can do it in a matter of weeks without having to develop anything. Next, we will talk about what Pentesting is, what you can achieve and some tools to learn this attractive skill.
Pentesting manages to expose vulnerabilities through attacks on an organization or whatever target it was. These tests are aimed at the IT area (Information Technology), to check the security of the entire network and of the different systems in the company. The results obtained help us to know which vulnerabilities should not escape us, and correct them as soon as possible. Thanks to Pentesting, we will be able to know about what can be done regarding them to mitigate possible attacks, as far as possible.
On the other hand, it is possible to identify and quantify risks in everything we do. Not only does it allow you to create cybersecurity policies, but it also allows you to identify opportunities for future training. In addition to action plans to correct these vulnerabilities. Let us remember that cyberattacks, both against people and organizations, occur with increasing frequency. Consequently, the value of what is lost is very high. Losing or exposing personal or other data can leave consequences that are difficult to cope with.
Just as there are many courses, workshops and tutorials to learn and improve, we must also share what we have learned and why not, our experiences. In this way, we help the Pentesting field to really improve. The skills and tools to confront cyber attackers cannot be left behind. These are the ones who are preparing by leaps and bounds to cause more and more severe damage.
Of course, we must pay attention when we disclose our Pentesting results or experiences. Since a lot of data can expose personal or corporate information, which could generate unnecessary risks. For example, it can be shared in relation to the number of people who are on your team (if you have it). You can also the frequency with which you carry out these tests and the chosen tools.
Recommendations of programs and tools for Pentesting
In RedesZone we are going to make a list of fundamental programs and tools to start in the world of Pentesting, logically these tools are more than used and known by experts.
VMware and VirtualBox
Your main ally when performing Pentesting activities will be a virtual machine. Both VMware and VirtualBox will allow us to create virtual machines with real operating systems to train ourselves, and also to install Pentesting-oriented operating systems such as Kali Linux and other Linux distributions with similar purposes. An important detail is that VMware is a paid solution, while VirtualBox is a completely free solution.
Both programs will be essential for testing and learning, from their official websites you can find all the details about both solutions and the download links.
Kali Linux
This is the best known Pentesting and Ethical Hacking operating system. It has an extensive list of tools to get you started. If you want to know what tools it contains, you can visit the official site where you will find a detailed list of those that are available. Kali Linux has the following tools for conducting IT security audits:
- To collect information
- Vulnerability scan
- Attacks on wireless networks
- Web applications
- To take advantage of vulnerabilities
- Computer forensics
- Stress testing
- Sniffing and spoofing
- Password attacks
- Reverse engineering and more.
You can access the official site here to download the latest version and access the support you need for tools and procedures.
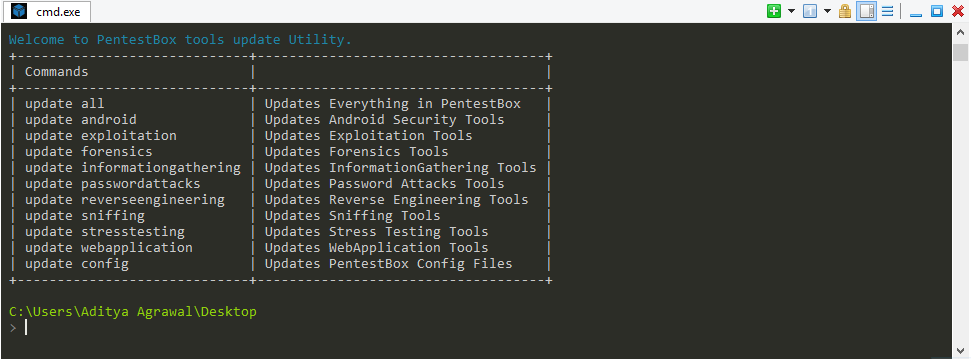
PentestBox
PentestBox is a penetration testing tool that works directly on Windows operating systems. It is designed for the simplicity and variety of options to run our tests. It is worth noting that it is free of charge, and it is compatible with several popular tools such as WireShark, Nmap, John The Ripper and others. One of its peculiarities is that it runs through the command line (cmd).
If you want to start Pentesting faster, without going through the download and installation steps, it is a very good alternative if your main operating system is Windows.
Also, it is portable. This means that your entire test environment can be taken with you when you need it, no installation required. It will not be necessary to make any adjustments to the configurations and dependencies. The PentestBox itself will take care of that. You only have to choose the storage device that you will use to carry. It can even be a pendrive.
OWASP’s Testing Guide
If you are interested in delving into the world of web applications, this book will be of great help. Stands for OWASP mean OWASP is an open community with global reach. Its main purpose is to improve application security, as well as to make available to all stakeholders what one must know to be successful in the industry. The success we are talking about does not only refer to when carrying out tasks, but also when making decisions if we have planned to implement some security measures.
All materials, including this one, are permanently free. In addition, they are licensed so that you can freely copy, distribute or broadcast. If necessary, you can modify or adapt the content to suit different audiences or needs, always respecting the roots and principles of OWASP.

Now, what good is a digital book to me? It is very useful because books, as well as the large number of courses available on the Internet, is one of the keys to achieving excellence.
Are you interested in more? You can access a large number of online courses on platforms such as Openwebinars and also Udemy, ideal for learning new techniques, or improving the techniques you already know. We are sure that with this guide you will have everything you need to get to the action. Remember, it is not necessary to cover the entire scope of Pentesting right out of the box. Rather, go ahead with small groups of commandos until we reach the level we want to reach.