All methods to crack the WPS of WiFi routers
WPS (Wi-Fi Protected Setup) is a method of connecting to WiFi networks that is insecure by nature, currently you can only use WPS to connect to WiFi networks protected with WPA and WPA2, however, WPS disappears completely with the WPA3 protocol to provide greater security to WiFi networks. The WPS can be cracked by different methods that we have today, some more complicated and others easier. If you want to crack a WPA or WPA2 password, it is best to focus on cracking the WPS (Wi-Fi Protected Setup) of your router because it will be much easier and faster. Today in RedesZone we are going to explain how WPS works, and how it can be cracked.
How WPS works
WPS (Wi-Fi Protected Setup) is a method of connecting to WiFi networks that is based on entering a PIN number or pressing a button on the router. Normally both methods are in all routers, however, some manufacturers only allow pressing the router button, discarding authentication in the router by PIN.
The big problem with WPS comes with the introduction of the PIN number, because it can only have 8 digits as a minimum and as a maximumIn this way, we would have a number of combinations of 100,000,000 possibilities. However, by the very construction of the WPS, this WPS PIN is divided into two subPINs of four digits each, therefore, the probabilities are 10,000 for the first PIN and 10,000 for the second PIN, and these can be cracked. PIN separately, which greatly facilitates its brute force attack. Finally, according to the standard, the last digit of the PIN2 serves for the checksum of the rest of the PIN, therefore, it is not a key digit but is calculated based on the other 7 digits, for this reason, the number of combinations that a WPS PIN has is only 11,000 possibilities. Taking into account that we have 11,000 possibilities, brute force cracking is very feasible, and can be achieved in 48 hours maximum.
Some router manufacturers have incorporated into their routers a limit of failed attempts in the WPS, depending on the manufacturer and how they have programmed the firmware, we can enter the PIN about 5 times, later the router will block access to the WiFI network by WPS PIN definitively , and it can no longer be used. However, we have found that many operator routers do not have this protection, so we could easily and quickly violate them.
The other connection method is by pressing a button on the router, by pressing this button, any device that connects in a time between 60 and 120 seconds will be able to access the wireless network without the need to enter any PIN or password. This also has an intrinsic security problem, and it is that during this time we will be “vulnerable” to an intruder connecting to our network. There are currently programs that you can leave running and they could automatically connect to the router when we press the WPS button, and obtain the WPA-PSK or WPA2-PSK key, therefore, using the WPS with a button is also a risk for 60 or 120 seconds.
WiFiSlax: The Swiss Army Knife to Crack WPS
WiFiSlax is one of the Linux-based distributions most used for auditing wireless networks, whether they are networks with WEP, WPA, WPA2 encryption and they can also attack WPS (Wi-Fi Protected Setup). Currently, in WiFiSlax we have a large number of tools to attack the WPS by different methods, either by brute force, by dictionary with the PIN generator, and also with other methods such as the Pixie Attack attack.
Next, you can see all the tools currently available in WiFiSlax, to go to the WPS section you have to click on « Start / WiFiSlax / Wireless WPS «, as you can see here:
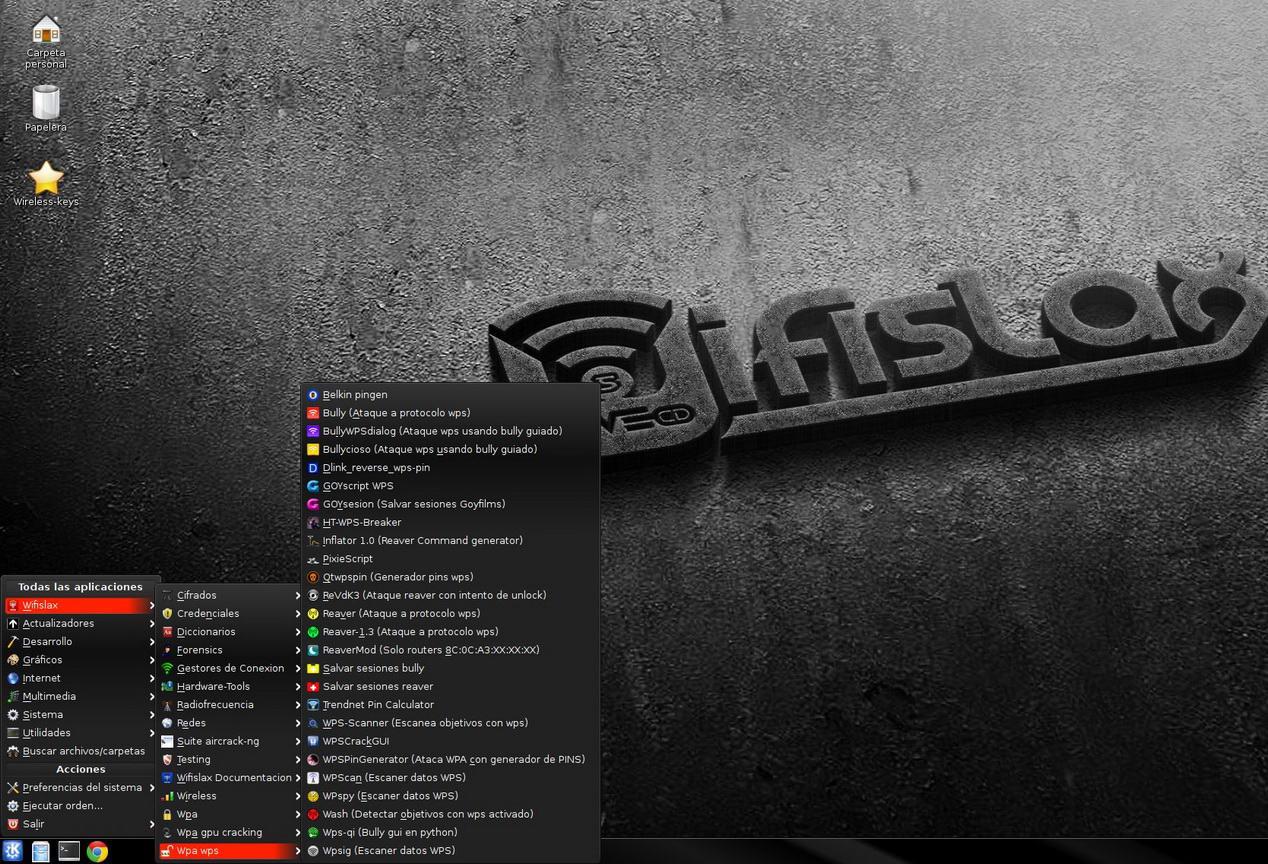
Once we have seen the WiFiSlax menu with all the tools, we are going to see what methods we can use to crack the WPS and what tools we can use. We are going to indicate the tools that we use for WiFi audits, because we currently have several programs (scripts) that do exactly the same functionality, but we will have different alternatives for you to choose.
Crack the WPS by dictionary
Some routers of the operators and also some routers that we can buy in the market, have a WPS PIN preconfigured at the factory. This means that a certain router has one or more preconfigured PINs that we can test, because if the user has not changed this preconfigured WPS PIN, we can directly enter the WiFi wireless network by testing several PINs that are well known.
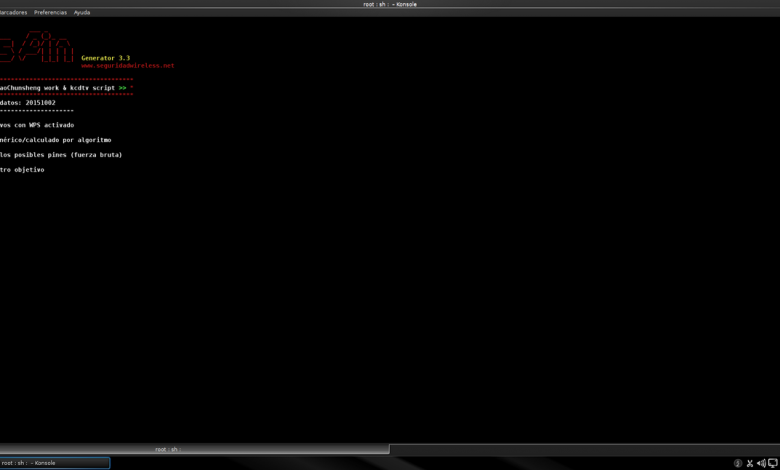
The WPSPinGenerator program (Attack WPA with PINS generator) is one of the best to attack WPS by dictionary. When executing it, we will have different options:
- Search for targets with WPS activated : this functionality will allow us to search for all the routers around us that have WPS activated. It is the first thing we will have to do.
- Test generic PIN / calculated by algorithm : once we have searched for all the targets with WPS activated, we can use this option to show us and the program test the PINs that we have in the PIN database. Thanks to this function, we can test 3 or 5 default PINs and crack the WPS in seconds, without the need to attack it by brute force.
- Test all possible pins (brute force) : this functionality will allow us to attack the WPS protocol through brute force, to test all possible PINs. Thanks to this, with this program we can attack the WPS by both methods (dictionary and brute force).
- Select another goal
- Leave
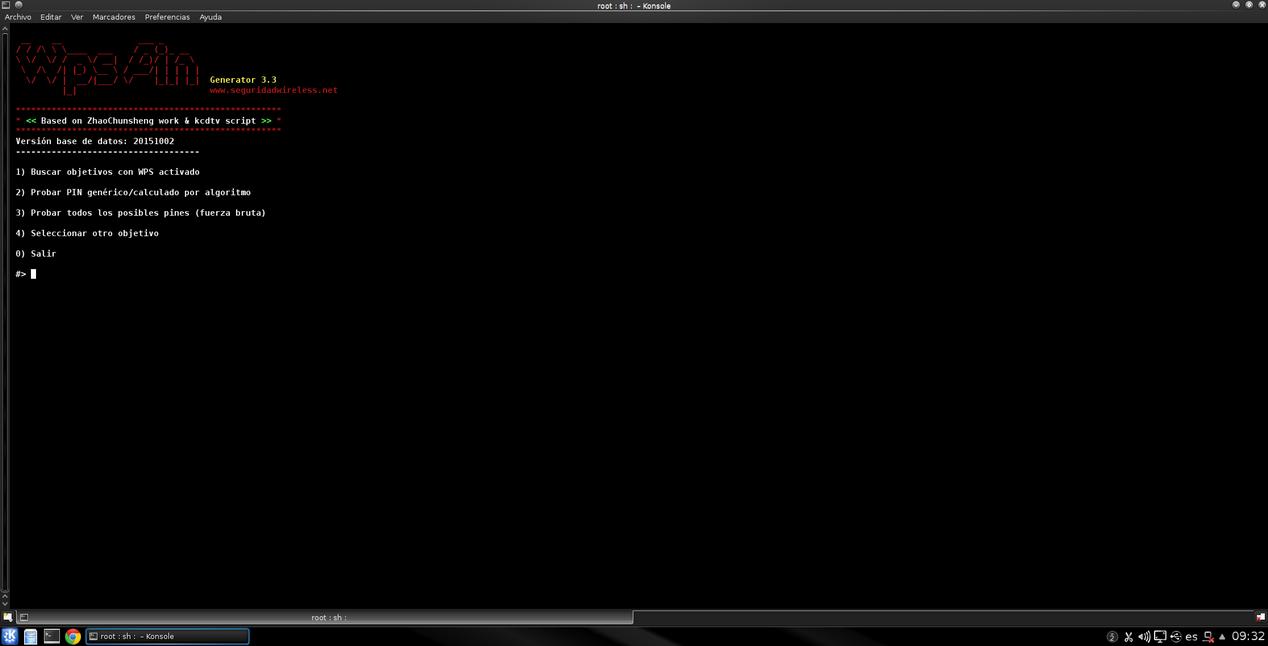
The operation of this program is really simple, since we will simply have to follow the configuration wizard via the console that you can see there. The only thing we will need is that our WiFi card supports WPS and is compatible with the operating system, currently the vast majority of cards with Realtek chipset are compatible.
With this dictionary attack, even if the router has a limit of attempts by WPS, it is very likely that we will get the WPA-PSK or WPA2-PSK key in very few attempts, before the router limits our attempts, therefore, this attack is one of the fastest we can do, as long as the router has default PINs by default.
Crack the WPS by brute force
This method of attacking the WPS has two main problems: the time, which can last up to 72 hours if you have bad luck with the PIN, and the limit of PIN attempts by the firmware of the router.
If our router has firmware with a limit of PIN attempts, depending on how the firmware is programmed, we will no longer be able to try PIN by brute force until the router restarts, although in some cases they only leave the WPS inoperative for a while (one hour, one day etc). However, it is worth trying to brute force the router to check whether or not we have the limit of PIN attempts.
Currently, we have many programs to attack the WPS through a brute force attack. For example, the previous program WPSPinGenerator can be used to attack by brute force, however, our favorite program is Bullyciosa, an all-in-one script that can:
- Detect the WPS in all the routers around us.
- Attacking the WPS by brute force is compatible both for PINs that do not include a checksum in the last digit of PIN2, as well as for those that incorporate the checksum, calculating it completely automatically.
Other characteristics of this program is that it will allow us to continue the WPS attack for the number that we want. Depending on the PIN that the router has, it can take from minutes to approximately 48 hours, it depends on the behavior of the WiFi network card with WPS, and also the WPS router, the distance against the WiFi access point, etc.
Crack the WPS with Pixie Dust Attack
Pixie Dust Attack is an attack on the WPS protocol that focuses on capturing the exchange of packets between the victim router and the attacker, to later crack the PIN offline, so it is much faster than attacking the WPS by dictionary or force brute, since, being able to crack it offline, it is much faster than depending on the exchange of messages between the router and the attacker. The PixieScript tool automates this process to achieve it in seconds, however, not all routers are compatible, and it is very likely that the manufacturer of the affected WiFi routers have already fixed this problem in the firmware, and have implemented the WPS in another way. Safer.
Another very interesting feature of PixieScript is that it incorporates a small database of the BSSIDs (wireless MACs) of the known access points affected, in fact, we can consult it from the script itself.
As you have seen, we can crack the WPS of WiFi routers in these three ways, the fastest is with the Pixie Dust Attack attack, but not all routers are affected by this problem in their WPS, then the fastest it would be dictionary using WPSPinGenerator and the default WPS PINs on the routers. Finally, the brute force attack can take hours, but we can achieve it with patience, unless the router limits the number of attempts and temporarily disables the WPS.